
Cybercriminals are evolving their tactics against small businesses. Instead of forcefully breaking in, they quietly gain access using stolen login credentials — your digital keys. This method, known as...

Don't Sign That IT Contract Until You've Asked These Questions Choosing the wrong IT provider isn't just an inconvenience, it's a liability. If your business is in the Inland Empire or Coachella Valley and you're...

Unexpected events like power outages, cyberattacks, hardware malfunctions, and natural disasters can strike without warning, causing severe disruption to small businesses. While many believe that simply having...
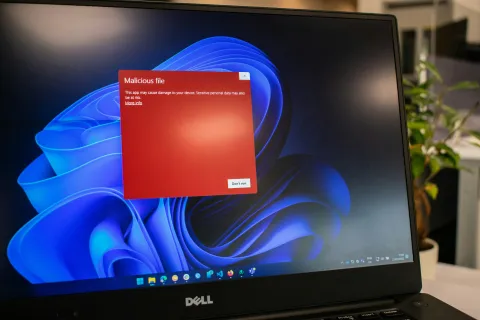
Why Business Continuity Planning Matters More Than Ever Downtime is more than an inconvenience; it's a threat to your bottom line. For small and midsize businesses (SMBs) in Southern California, a single IT...
Our smartphones accompany us everywhere, holding sensitive information like passwords and confidential business chats. Yet, the alarming reality is that phone tracking is surprisingly widespread and easier to execute...
Key Takeaways Email is still the #1 attack vector for cybercriminals—and small businesses are prime targets. Standard cloud email solutions are not enough to block modern threats like phishing,...

Many small business owners mistakenly believe that regulatory compliance concerns only large corporations. However, in 2025, that assumption is far from accurate. With regulations tightening across industries, small...
Key Takeaways Inland Empire SMBs face rising threats from BEC scams, ransomware, remote access vulnerabilities, insider risks, and AI-powered phishing. Small businesses are no longer flying under the...

You've probably heard the phrase: You get what you pay for. This is especially true in the world of IT. At first glance, opting for a low-cost managed IT service might look like a smart move—lower monthly...